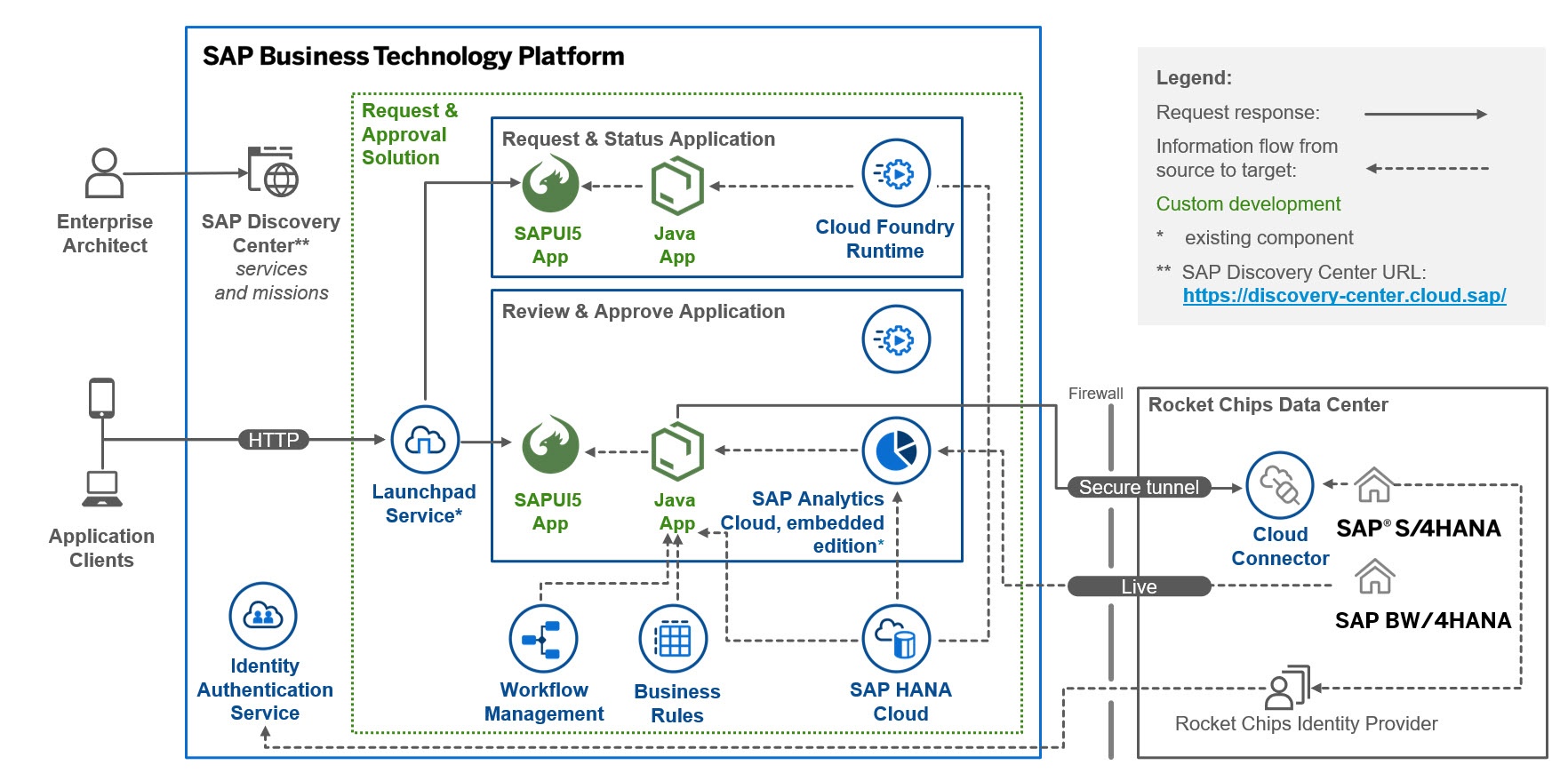
As the world becomes increasingly digital, businesses are rapidly adopting cloud platforms like SAP Business Technology Platform (BTP) to drive innovation, efficiency, and growth. However, with the rise of cyber threats and data breaches, ensuring the security of applications and data on these platforms is crucial.
In this comprehensive blog post, we’ll explore the best practices for securing SAP BTP environments from a user’s perspective. We’ll dive into the shared responsibility model, discuss common vulnerabilities, and provide actionable steps to fortify your SAP BTP landscape.
Understanding the Shared Responsibility Model in SAP BTP Security
When it comes to security in the cloud, it’s essential to understand the shared responsibility model. SAP BTP provides a robust foundation with built-in security features like identity and access management, data encryption, and network security. However, as a user, you are responsible for securing your custom applications and ensuring that they are developed and deployed securely.
It’s like building a house – SAP BTP provides the land, foundation, and basic structure, but you are responsible for designing, furnishing, and maintaining the interior to suit your needs. By understanding this model, you can effectively allocate resources and responsibilities to maintain a secure environment.
Navigating the OWASP Top 10 in SAP BTP Security
The Open Web Application Security Project (OWASP) Top 10 is a widely recognized standard that identifies the most critical web application security risks. As a user, it’s crucial to understand these vulnerabilities and take proactive measures to mitigate them in your SAP BTP applications.
Here’s a quick overview of the OWASP Top 10 and how they relate to SAP BTP:
| Vulnerability | Description | Mitigation Strategies |
|---|---|---|
| Injection | Occurs when untrusted data is sent to an interpreter as part of a command or query, potentially allowing attackers to execute malicious code. | Use parameterized queries, input validation, and secure coding practices. |
| Broken Authentication | Vulnerabilities in an application’s function related to authentication and session management. | Implement strong authentication mechanisms, such as multi-factor authentication, and follow best practices for session management. |
| Sensitive Data Exposure | Occurs when an application doesn’t properly protect sensitive data, such as credit cards, social security numbers, and authentication credentials. | Encrypt data at rest and in transit, and follow best practices for data storage and handling. |
| XML External Entities (XXE) | Occurs when an application processes XML input containing a reference to an external entity. | Use a secure XML parser and keep XML processors up to date. |
| Broken Access Control | Restrictions on what authenticated users are allowed to do are not properly enforced. | Implement robust access control mechanisms, such as role-based access control (RBAC), and regularly review and update permissions. |
| Security Misconfiguration | Occurs due to insecure default configurations, incomplete or ad-hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information. | Follow SAP’s security configuration guidelines, regularly review and update configurations, and avoid exposing sensitive information in error messages. |
| Cross-Site Scripting (XSS) | Occurs when an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript. | Implement input validation, output encoding, and use security headers like Content Security Policy (CSP). |
| Insecure Deserialization | Occurs when an application deserializes untrusted data, which can result in remote code execution, replay attacks, injection attacks, and privilege escalation attacks. | Use secure deserialization libraries, validate and sanitize input, and implement integrity checks. |
| Using Components with Known Vulnerabilities | Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application, which can result in serious impact. | Keep all components up to date and use a software composition analysis tool to identify and remediate vulnerabilities. |
| Insufficient Logging and Monitoring | Insufficient logging and monitoring, coupled with ineffective incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. | Implement robust logging and monitoring, and have an effective incident response plan in place. |
In Summary
By understanding and addressing these vulnerabilities in your SAP BTP applications, you can significantly reduce the risk of security breaches and protect your business.
Implementing Secure Development Practices in SAP BTP Security
Developing secure applications is crucial to maintaining a robust security posture in your SAP BTP environment. Here are some best practices to keep in mind:
- Follow secure coding standards: Adhere to industry-recognized secure coding standards, such as the OWASP Secure Coding Practices Quick Reference Guide, to ensure that your code is free from common vulnerabilities.
- Perform input validation: Implement robust input validation mechanisms to prevent injection attacks and other vulnerabilities. Validate all user input, including form fields, URL parameters, and headers.
- Implement secure authentication and authorization: Use strong authentication mechanisms, such as multi-factor authentication, and follow best practices for session management. Implement role-based access control (RBAC) to ensure that users have the appropriate level of access to resources.
- Handle errors securely: Ensure that your application handles errors gracefully and doesn’t expose sensitive information in error messages. Use a centralized error handling mechanism to maintain consistency and control.
- Implement logging and monitoring: Implement robust logging and monitoring mechanisms to detect and respond to security incidents. Use tools like the SAP Audit Log Viewer service to centralize and analyze logs.
- Perform regular security testing: Conduct regular security testing, such as penetration testing and vulnerability assessments, to identify and address vulnerabilities in your SAP BTP applications. Use tools like the SAP Malware Scanning service to scan business documents for malware.
- Keep components up to date: Regularly update all components, including libraries, frameworks, and operating systems, to ensure that they are free from known vulnerabilities. Use a software composition analysis tool to identify and remediate vulnerabilities.
Handling Data Securely
- Implement secure data handling: Encrypt sensitive data at rest and in transit, and follow best practices for data storage and handling. Use the SAP Credential Store service to securely store passwords and keys for applications running on SAP BTP.
- Secure network communication: Use secure protocols, such as HTTPS, to encrypt network communication between your applications and external services. Use the SAP Custom Domain service to make SAP BTP applications accessible via a personalized domain and manage certificates and trust.
- Maintain a secure development lifecycle: Implement a secure development lifecycle that includes security requirements, threat modeling, secure coding practices, and security testing. Use tools like the SAP Cloud Application Programming Model (CAP) to automatically enforce authorization in CAP-supported runtimes like Node.js and Java.
By following these best practices, you can significantly reduce the risk of security breaches and protect your business in the cloud.
Partnering with Security Experts for SAP BTP Security
While implementing secure development practices is crucial, partnering with security experts can provide additional benefits. Security experts can help you identify and mitigate vulnerabilities, conduct security assessments, and provide guidance on best practices.
RedRays, for example, is a company that specializes in SAP BTP security. They offer services like application security audits, penetration testing, and security consulting to help businesses secure their SAP BTP environments.
By partnering with security experts, you can:
- Gain access to specialized knowledge and expertise
- Identify and mitigate vulnerabilities more effectively
- Ensure compliance with industry standards and regulations
- Reduce the risk of security breaches and protect your business
Conclusion
Securing SAP BTP environments is a critical priority for businesses in today’s digital landscape. By understanding the shared responsibility model, navigating the OWASP Top 10, implementing secure development practices, and partnering with security experts, you can significantly reduce the risk of security breaches and protect your business in the cloud.
Remember, security is an ongoing process, not a one-time event. Stay vigilant, keep your applications and components up to date, and regularly review and update your security measures to maintain a robust security posture.
Also Read: When to Use SOAP Adapters in SAP CPI: A Developer’s Guide – Tech News Before It’s News | Shift GearX
If you liked this article, please share it and subscribe to my website. For consulting work, please visit my website, Shift Gear and I would be glad to help you in your requirement.
Also Read: SAP CPI: A Guide to Setting Up Outbound SOAP Web Services – Tech News Before It’s News | Shift GearX